Remember the huge debacle of FTAs (file type associations) we’ve discussed on this blog a few times previously? Remember how Microsoft have made it so horribly difficult to set or enforce or roam a specific FTA for different sets of users? Remember how the article I wrote showed you how to do it by removing Registry values (rather backwardly)? Well, this is only good news if you’re an AppSense customer, but if you are, you can now manage your FTAs directly from Environment Manager.
AppSense Environment Manager version 10 now ships with a nifty File Type Association action which sits under Actions | File and Folder | File Type Associations.
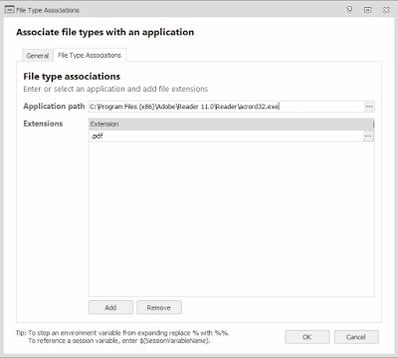
As you’d expect, it’s very easy to set up. Simply put in the path to the application you want to associate with the filetype, and specify the filetype itself (including the preceding period – e.g. .pdf)
Then you can easily set up Conditions to complement these Actions, as in the example below where we have applied a different PDF FTA for each of three different AD security groups
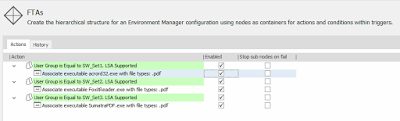
Enforcing FTAs is as simple as that – whenever a user logs in the FTA you have defined is applied to them, based around the huge set of Conditions available in the EM console. You could even set it up so that the FTA is applied only if the actual program exists on the endpoint (see below)
However, if you wanted to roam FTAs you are now approaching the limitations of Microsoft’s new rules which are discussed in the previous article. But you could still do this in AppSense Environment Manager with a bit of cleverness…
- You would need to capture any custom user-defined FTAs by monitoring if the value ProgId exists in HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.pdf\UserChoice (using PDF as the example here) at logoff time
- If it does, capture the value from here and save it somewhere (flag file, Registry value, Personalization Server, the choice is yours)
- At next logon, read the flag file or value and use that as a trigger to set the FTA to the required application.
I will see if I can document a process for doing this and post it as an update to this article.
But anyway – at least AppSense have given us a surefire way for enforcing particular FTAs on Windows 8/Server 2012 R2/Windows 10/Server 2016, which is taking us back to the good old days when we could do this via Group Policy Preferences. Ironic isn’t it – GPP used to be able to do this flawlessly, whereas with AppSense you were reduced to scripting (see this article). But now, Group Policy can only enforce them on a device level (useless for multi-user systems or shared devices), and AppSense can do it natively. How progressive is that?