When you are using AppSense Application Manager to block unknown executables and secure your environment, a key part of your arsenal is the Application Manager Rules Analyzer. It has hardly changed since the first time I wrote about it, although I understand the latest versions of AppSense (possibly the 10.1 release) will have a feature whereby the blocking rule is actually written out to the event log along with the “execution denied” event. That’s all very cool and will be hugely useful, but for those of us who aren’t able to go to the latest release yet, you sometimes might need to enable the Rules Analyzer with a script.
Situations where this would be useful are where you have endpoints that, for whatever reason, don’t seem to work with the Application Manager Console as far as enabling Rules Analyzer goes. Normally, to enable Rules Analyzer logging you need the following conditions to be fulfilled:-
- AppSense agents installed and running on the device
- Admin access to the endpoint via the account that is running the AM Console (access to the admin$ and c$ shares)
- Remote Registry service running on the endpoint
- Firewall ports opened for AppSense services (see this article for a rundown)
- DNS resolution working to the endpoint
However, you may find occasional situations where all of the above seem to be correct, but for some unknown reason, enabling Application Manager Rules Analyzer logging through the console repeatedly fails. I’m pretty sure that they all tend to be related to firewall rules at one end or the other, but sometimes you don’t have the time, resource or even the permissions to perform detailed analysis and then submit the required changes for approval. What would be nice is a quick easy way to turn on the logging on the endpoint without needing the console to be working perfectly, and then gather the log files for perusal.
I’d love to claim that I came up with this technique myself, but sadly, the nice people over at AppSense support pointed me in the direction of this article that they penned last year. However, what I’ve done is simply automate the process itself so that you can point it at a particular device and then enable or disable it. I’ve also pretty much assumed that people who are using AppSense Application Manager will probably also be using Environment Manager (although I am sure there are places that use AM without EM), so I’ve created a downloadable configuration to enable this as two Start Menu shortcuts, one to start logging and one to stop the logging.
The exact commands you can use to start and stop the logging differ ever so slightly between versions of Application Manager. For 8.6 or 8.7 use the following commands:-
8.6 or 8.7 start Rules Analyzer logging
# To start logging
$OutputPath = “$env:AllUsersProfile\AppSense\Application Manager\Rules Analyzer”
@”
<EndpointCommand ClassName=”AM.EndpointCommand.0806″ Destination=”localhost” CommandType=”RulesAnalyzerStartLogging” />
”@ | Out-File “$OutputPath\console.command“
$OutputPath = “$env:AllUsersProfile\AppSense\Application Manager\Rules Analyzer”
@”
TRIGGER
”@ | Out-File “$OutputPath\console.command.trigger“
stop-service “AppSense Application Manager Agent”
start-service “AppSense Application Manager Agent”
8.6 or 8.7 stop Rules Analyzer logging
# To stop logging
$OutputPath = “$env:AllUsersProfile\AppSense\Application Manager\Rules Analyzer”
@”
<EndpointCommand ClassName=”AM.EndpointCommand.0806″ Destination=”localhost” CommandType=”RulesAnalyzerStopLogging” />
”@ | Out-File “$OutputPath\console.command“
$OutputPath = “$env:AllUsersProfile\AppSense\Application Manager\Rules Analyzer”
@”
TRIGGER
”@ | Out-File “$OutputPath\console.command.trigger“
stop-service “AppSense Application Manager Agent”
start-service “AppSense Application Manager Agent”
For 8.8 or 8.9. you need to use the following commands, which differ only in the version number of the file’s content
8.8 or 8.9 start Rules Analyzer logging
# To start logging
$OutputPath = “$env:AllUsersProfile\AppSense\Application Manager\Rules Analyzer”
@”
<EndpointCommand ClassName=”AM.EndpointCommand.0808″ Destination=”localhost” CommandType=”RulesAnalyzerStartLogging” />
”@ | Out-File “$OutputPath\console.command“
$OutputPath = “$env:AllUsersProfile\AppSense\Application Manager\Rules Analyzer”
@”
TRIGGER
”@ | Out-File “$OutputPath\console.command.trigger“
stop-service “AppSense Application Manager Agent”
start-service “AppSense Application Manager Agent”
8.8 or 8.9 stop Rules Analyzer logging
# To stop logging
$OutputPath = “$env:AllUsersProfile\AppSense\Application Manager\Rules Analyzer”
@”
<EndpointCommand ClassName=”AM.EndpointCommand.0808″ Destination=”localhost” CommandType=”RulesAnalyzerStopLogging” />
”@ | Out-File “$OutputPath\console.command“
$OutputPath = “$env:AllUsersProfile\AppSense\Application Manager\Rules Analyzer”
@”
TRIGGER
”@ | Out-File “$OutputPath\console.command.trigger“
stop-service “AppSense Application Manager Agent”
start-service “AppSense Application Manager Agent”
This should be done with administrative privileges (to enable the service restart).
Once you do this, it will start logging the results of Rules Analyzer out to %ALLUSERSPROFILE%\AppSense\Application Manager\RulesAnalyzer\RulesAnalyzerlog.xml. You can then view these results by using the Import command in the Application Manager Console. You need to add an endpoint before you can access the Import command, but it doesn’t have to be the problem device or devices (which is good because I normally need to use this when endpoints simply won’t connect in the console!) Just add one endpoint, and then you can use the Import command
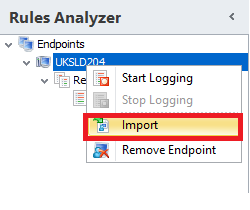
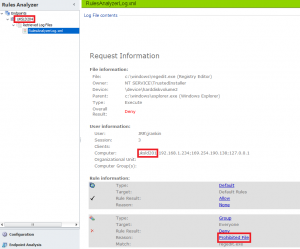
You can then simply browse across to the endpoint and grab the XML file for perusal, or if it’s in an area inaccessible by direct SMB share connection, have the user copy it off somewhere or send it across to you for investigation. In the image below showing the results, I have also highlighted the endpoint name that we are connected to and the endpoint that is providing the logging info, just to show they are indeed different.
This can be provisioned onto an endpoint in many different ways – the scripters amongst you might want to make some changes so that you could maybe supply a remote computer name or array of computer names to pass in, so that it could maybe be done en masse instead of just on particular endpoints. It’s up to you what you can do with this technique. What I have done, though, if you’re an AppSense Environment Manager user as well, is create a quick configuration that creates two shortcuts on the user’s Start Menu for “start logging” and “stop logging”. Log files can get pretty big pretty quickly, so it’s ideal to be able to enable the logging for just long enough so that the user can recreate their issue, and then stop it again.
What was interesting was that I used the old “blank executable” trick in this configuration to set up the shortcuts. However, on Windows 10 1607, the csc.exe command that creates the blank executable no longer works properly. Not sure what’s causing it – when run as SYSTEM the csc.exe command crashes with a “file too long or invalid” error. However, what does still work is the native PowerShell method created by AppSense themselves, so it’s listed in the configuration. Of course you could just create the file manually and copy it across, or drop it in the base image, or even run the PowerShell commands directly if you can spawn them with administrative rights – up to you!
The configuration is available for download here, and I tested this on Windows 10 1607, which should make it fully backward-compatible.
So, here’s hoping this is a useful technique for enabling AppSense Application Manager Rules Analyzer logging either by the user on request, or for endpoint devices that, for whatever reason, can’t be contacted by the console.


