Wow! I’ve been so busy lately, I’ve been unable to complete some of the articles I’ve been drafting for ages. I’ve got some great stuff in the pipeline, but in between doing presentations, writing articles, attending conferences, beta testing, day-to-day work and of course trying to spend time with my family, blogging has been sadly neglected.
To counter this, I’ve decided to try and do a bit of a series on something I seem to be seeing more and more questions about – Windows 8.x, and managing it from an EUC perspective (using AppSense obviously, but not exclusively). Rather than hammer everything into one article, I thought I’d flesh it out a bit, simply to try and avoid another period of sad neglect for my loyal readers!
Update – I’ve found an EM-based solution for this, see the last section of the article prior to the Summary.
The repulsive Charms Menu
| Charmless |
One of the first (and most annoying) things that I quickly found out about Windows 8.x (I’m doing all my testing on 8.1, for the record), is that it has not been policy-enabled particularly well, or even remotely comprehensively. It’s true that meaningful corporate restriction GPOs often lag behind versions of Windows quite dramatically, but this is Windows 8.1 Update 1, and that seems far enough ahead of the 8.0 curve to have addressed this by now.
The worst thing is, though, the Charms menu seems to actually offer users a way of circumventing settings that have been deployed via Group Policy. Yes, you can actually use the Modern UI to poke holes in your carefully-constructed corporate policies which protect users from themselves. Need an example? Well, the first one I could dig up was this.
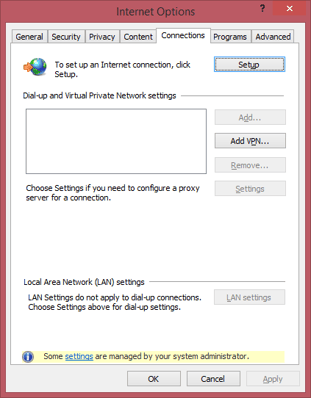
Use Group Policy Preferences to set the proxy server for Internet Explorer, by using the Registry setting for ProxyServer in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings. Then use the Group Policy Object User Configuration | Policies | Administrative Templates | Windows Components | Internet Explorer | Disable Changing Connection Settings to lock it down, effectively disabling the entry point for LAN Connections in Internet Options.
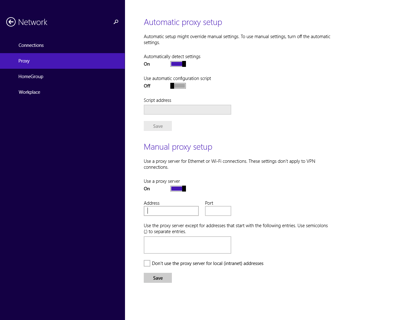
All well and good – until the user swipes up their pesky Charms Bar. Go to Settings, | Change PC Settings | Network | Proxy. What do we see?
Yes, you can change the proxy with impunity, effectively circumventing the GPO.
Now, hold onto your horses – this is just an example, so before you start screaming about WPAD config files and telling me how any app that doesn’t use the correct proxy shouldn’t be able to find a way out to the big bad Intertubes, take a moment to think. The most worrying possibility is that this is just the first example I could find of there being a hole that users could slip through GP-wise by using the Charms bar. Mitigate this particular one through other technologies, and you may find there are many others that have slipped under the radar unnoticed.
Group Policy Objects
There are GPOs for Windows 8.x/Server 2012, this we know. Surely there must be one that lets us block access to the Charms bar?
Unfortunately – no, there’s not. But there is something that may offer some hope. It is the setting for User Configuration | Administrative Templates | Control Panel | Prohibit access to Control Panel and PC settings. If we can’t kill the Charms bar itself, we can stop access to the PC settings link, yes?
However, this GPO goes far above and beyond what we want. You can’t access PC settings…as you can see below, the link has disappeared now that the policy is active…
…but there are further side-effects to defining this policy. For instance, try getting into Control Panel via any of the entry points…
…and you will find you’ve been unceremoniously blocked. Effectively, if I restrict access to PC settings from the Charms bar, I also kill Control Panel completely. As my users generally like (and need, to be fair) to access parts of Control Panel, such as Accessibility, Mouse, Keyboard, etc., this is a total non-starter.
Software Restriction Policies/AppLocker/Application Manager
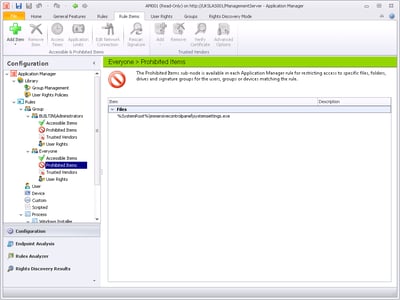
Next up is a thought that maybe you can restrict the execution of the PC settings link by using SRPs, AppLocker or even Application Manager. An interesting idea….let’s see what mileage it has.
The executable that runs when you open the PC settings link is %systemdrive%\Windows\ImmersiveControlPanel\SystemSettings.exe, and as this is an AppSense-focused site, we will restrict it using AppSense Application Manager. You could, though, quite easily do it through SRPs, AppLocker, or your application management software of choice.
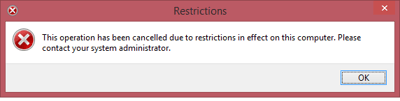
Once we’ve saved and deployed it through our mechanism of choice, we can then give this a whirl and see how it behaves.
Again, this is a disappointing outcome. It doesn’t display the normal Application Manager dialog box, the user isn’t given any indication that corporate policy is blocking them…all in all, not a suitable screen to be presenting a user with. Restricting the execution, whilst promising, doesn’t give us the results we need.
Now in Windows 8.1 Update 1 there is the Navigation tab in Taskbar and Navigation Properties, which has various options to do with the charms. Can we use this to help us?
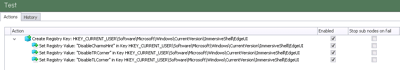
Firstly, we need to find the Registry values that these options refer to, so that we can deploy them without touching every endpoint manually. Again, Group Policy Objects would be so helpful here. A bit of digging reveals the pertinent Registry locations, so we will now bundle them into Environment Manager and deploy. The keys and values we need are
Keys
HKCU\Software\Microsoft\Windows\CurrentVersion\ImmersiveShell\EdgeUI
Values
DisableCharmsHint, REG_DWORD, 1
DisableTRCorner, REG_DWORD, 1
DisableTLCorner, REG_DWORD, 1
Here is the EM configuration we will use to push these out, but it could be done in any one of many ways
In this case, the main “hot corners” are all successfully disabled – but there are still a couple of Charms bar entry points active. If you move to the bottom right-hand corner and swipe up, or if you use Win+C, the menu appears. So this, although it helps us out by killing the other “hot corners” (some useful progress), we’re still not where we want to be, which is blocking access to it completely. Hmmm.
Environment Manager lockdown
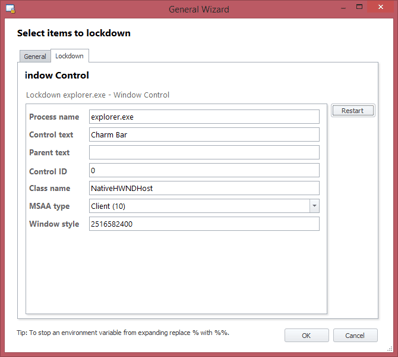
We can definitely block the Win+C keyboard shortcut using Environment Manager Lockdown items – so maybe this is the path to choose. Can we use the General Lockdown tool to exterminate the Charms bar completely?
At first glance, it seems promising. The Spy Tool seems to pick up the Charms bar successfully…
Third-party tools
This is always a bit dodgy, particularly in enterprise environments, but given that there are no scripted techniques I can find for manipulating the Charms bar, this is where we’ve arrived. (Update – Self-Heal in EM can handle this – see the last section)
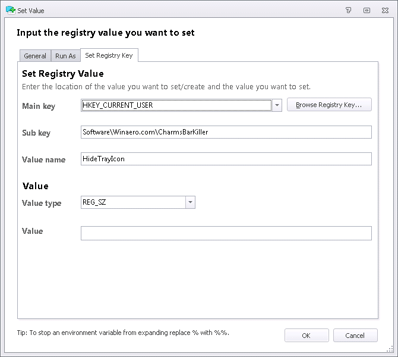
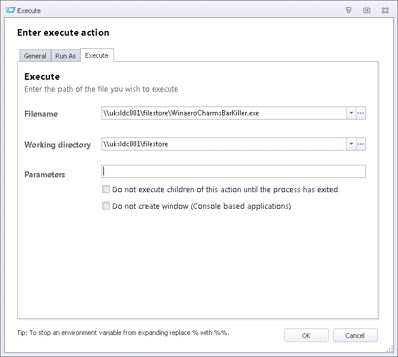
Googling allows us to find that WinAero have a program called the Charms Bar Killer. It seems to work nicely enough – all we need to do is put it either in the base image or on a network share, and then set some Registry keys to auto-hide it.
First we set the Registry value so it auto-hides when executed (a blank value is what’s required, this isn’t an error)
Now it’s down to testing again….and this time, we finally have blocked the entry point to the Charms bar! Hot corners, the swipe from bottom right, the Win+C key combination – all of these entry points are now blocked. Thank [deity] for that!
When the user logs in, the executable launches but is hidden from the notification area. It can be seen in Task Manager, but don’t worry if the user inadvertently ends the process – the Charms Bar will stay locked away unless the user restarts explorer.exe in addition to ending the process. Handy!
Update 30/10/14 – Self-Heal
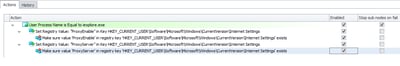
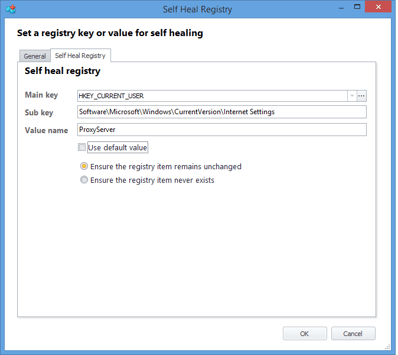
Actually, as I found out just today, you can actually do this natively through AppSense Environment Manager – by using Registry Self-Heal items. Simply set the relevant settings (in this case, ProxyEnable and ProxyServer in HKCU\Software\Microsoft\Internet Settings), and then underneath them nest a Self-Heal Action that prevents them from being changed. Observe below
Once you’ve deployed this, users can change settings and save them through the Charms menu – but as soon as you re-open it, they’ve changed back to the original settings. Awesome EM power!
Summary
The main conclusion that can be drawn from this is that it’s very hard to make certain parts of the Modern UI acceptable for corporate deployment. However, the EM Self-Heal Action – or the third-party way, if you want to kill the whole thing – should allow you to keep this security hole from appearing, for now. Win!
I’m hoping Microsoft expand the GPOs available or make some part of the user interface able to hide the Charms bar. Maybe something for Windows 8.1 Update 2? But until then, AppSense EM or the third-party tool are the only ways I could find to do it.
Anyway, I hope this is useful to some of you out there….more Windows 8.1 articles coming very soon, in addition to getting some of my half-finished stuff finally published 🙂